How do I set up a site-to-site VPN between a QuWAN device and an AWS VPC?
Applicable Products
Hardware
- QHora-301W
- QHora-321
- QHora-322
- QMiroPlus-201W
- QMiro-201W
Software
- QuWAN Orchestrator
- QuRouter 2.4.0 and later
- An Amazon Web Services (AWS) account
Details
This tutorial explains how to configure a route-based VPN between a QuWAN SD-WAN device and an AWS virtual private cloud (VPC). In a route-based VPN, the QuWAN device establishes an IPsec tunnel to the AWS virtual private gateway, and traffic is routed between the on-premises network and the AWS VPC using defined route tables. Only QNAP routers that have been added to QuWAN Orchestrator can be used for this setup. QuWAN Orchestrator manages the tunnel, handles routing, and maintains connectivity, while AWS routes traffic through the virtual private gateway, allowing secure, continuous communication between your network and cloud resources.
The steps cover configuring AWS VPC components, creating and attaching VPN gateways, downloading the AWS VPN configuration file, and applying the corresponding settings in QuWAN Orchestrator.
- QuWAN site-to-site VPN only supports IKEv2.
- Both devices (QuWAN device and AWS VPC) must use the same configuration settings for the VPN to function correctly.
- Your QNAP device must be added to QuWAN Orchestrator before configuring the site-to-site VPN. To add your QNAP device to QuWAN Orchestrator, see the Configuration chapter in the QuWAN and QuWAN Orchestrator Web Help.
Implementing a site-to-site VPN introduces additional complexity to your network. Ensure you understand the security implications before enabling it.
Procedure
Create a site-to-site connection VPN between your QNAP router and an AWS virtual private cloud (VPC)
A. Create a virtual private cloud
- Log in to https://console.aws.amazon.com/vpc/.
The VPC dashboard page appears. - Click Create VPC.
The Create VPC page appears. - Under VPC settings, select VPC only.
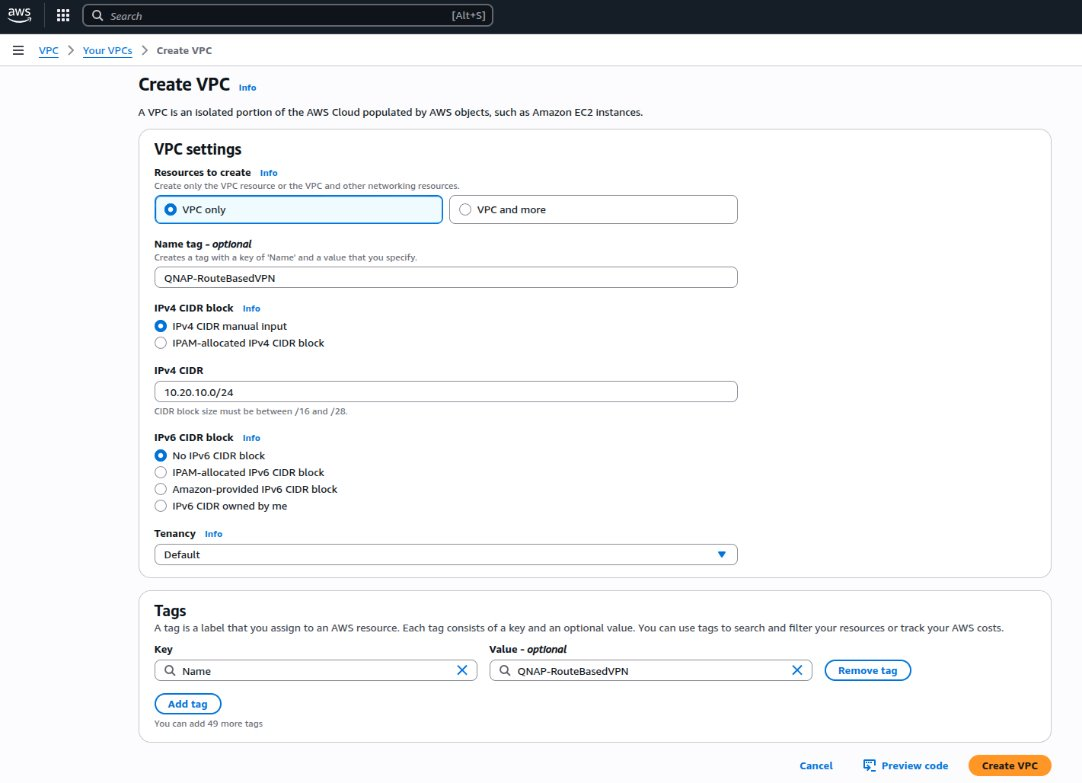
- Optional: Specify a name tag for the VPC, for example:
QNAP-RouteBasedVPN - Under IPv4 CIDR block, select IPv4 CIDR manual input.
- Specify the IPv4 address in CIDR format (e.g.,
10.20.10.0/24). - Under IPv6 CIDR block, select No IPv6 CIDR block.
- Optional: Select a tenancy option.NoteSelect whether EC2 instances in this VPC should use shared servers (default) or servers dedicated only to your account.
- Define one or more tags to help identify your resources, and assign a value to each tag.
- Optional: Click Preview code to visualize the relationships between the configured VPC resources.
- Click Create VPC.
AWS creates the VPC.
B. Create a subnet
- On the VPC dashboard side panel, go to Virtual private cloud > Subnets.
- Click Create subnet.
 The Create subnet page appears.
The Create subnet page appears. - Selected your VPC from the drop-down menu.
- Specify a name tag for the subnet.
- Optional: Select an availability zone from the drop-down menu, or keep No Preference to let AWS choose one.
- Specify the IPv4 subnet CIDR block.
- Optional: Define one or more tags to help identify the VPC subnet, and assign a value to each tag.
- Click Create subnet.
C. Create an internet gateway
- On the VPC dashboard side panel, go to Virtual private cloud > Internet gateways.
- Click Create internet gateway.
- Optional: Define one or more tags to help identify the VPC internet gateway, and assign a value to each tag.
- Specify a name tag for the internet gateway.
- Click Create internet gateway.
AWS creates the internet gateway. - Click Actions, and then click Attach to VPC.
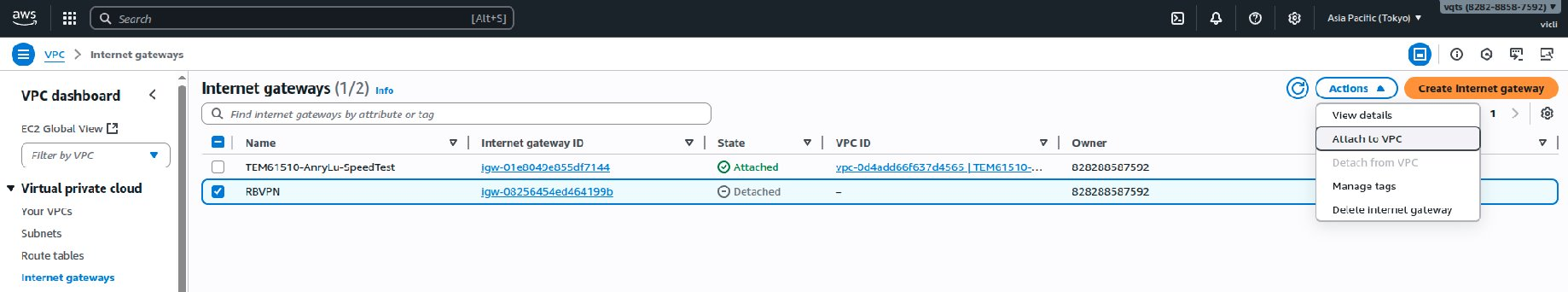 The Attach to VPC page appears.
The Attach to VPC page appears. - Click the search bar under Available VPCs, and then select the QuWAN VPC.
- Click Attach internet gateway.
AWS attaches the configured internet gateway to the QuWAN VPC.
D. Add the internet gateway to the route table
- On the VPC dashboard side panel, go to Virtual private cloud > Route tables.
- Identify the route table associated with the QuWAN VPC.
- Click the route table ID.
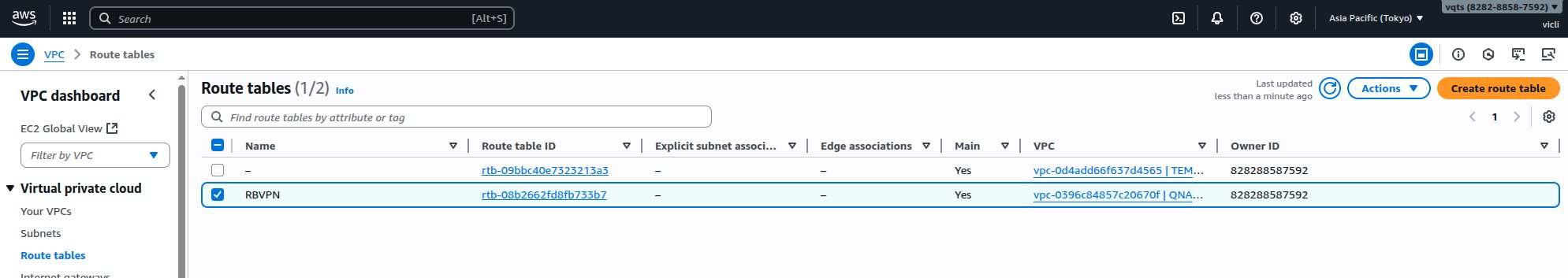 The route table page appears.
The route table page appears. - Click Edit routes.
The Edit routes page appears. - Click Add route.
- Enter
0.0.0.0/0as the destination. - Click the drop-down menu under Target, and select Internet Gateway.
A secondary field appears under Internet Gateway appears. - Select the previously configured internet gateway from the drop-down menu.
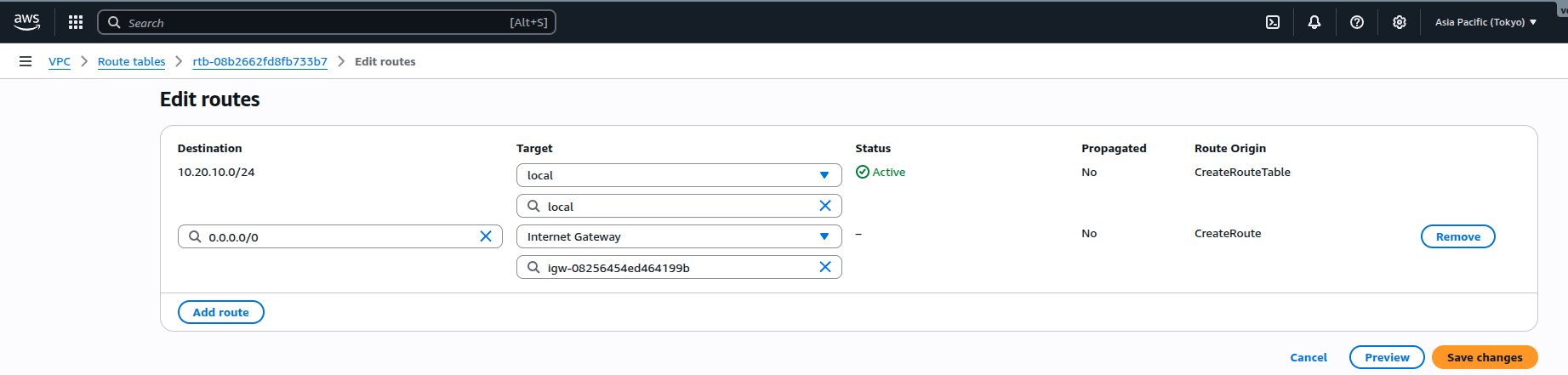
- Click Save changes.
AWS updates the route table.
E. Configure security groups for the VPC
- On the VPC dashboard side panel, go to Security > Security groups.
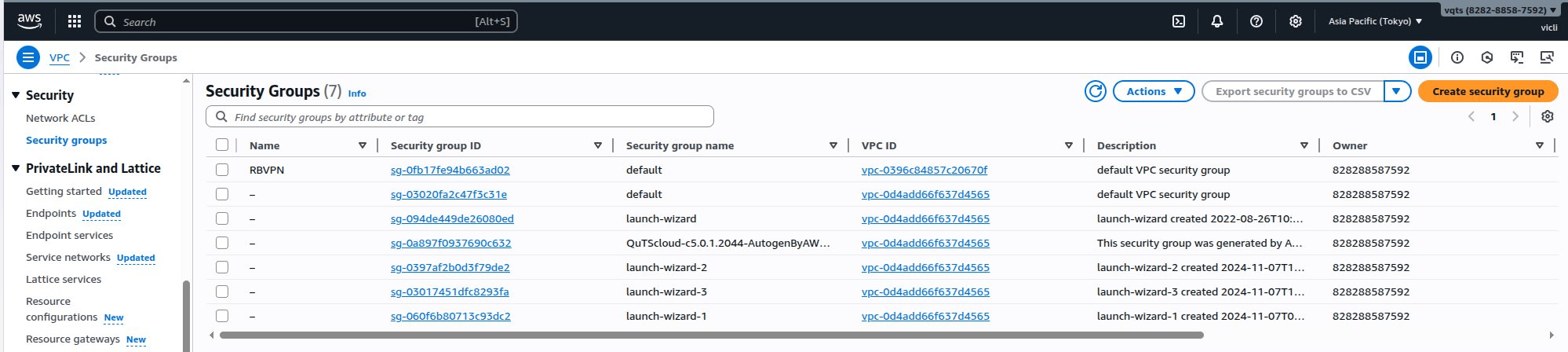
- Identify the security group associated with your VPC.
- Click the security group.
The security group page appears. - Click Edit inbound rules.
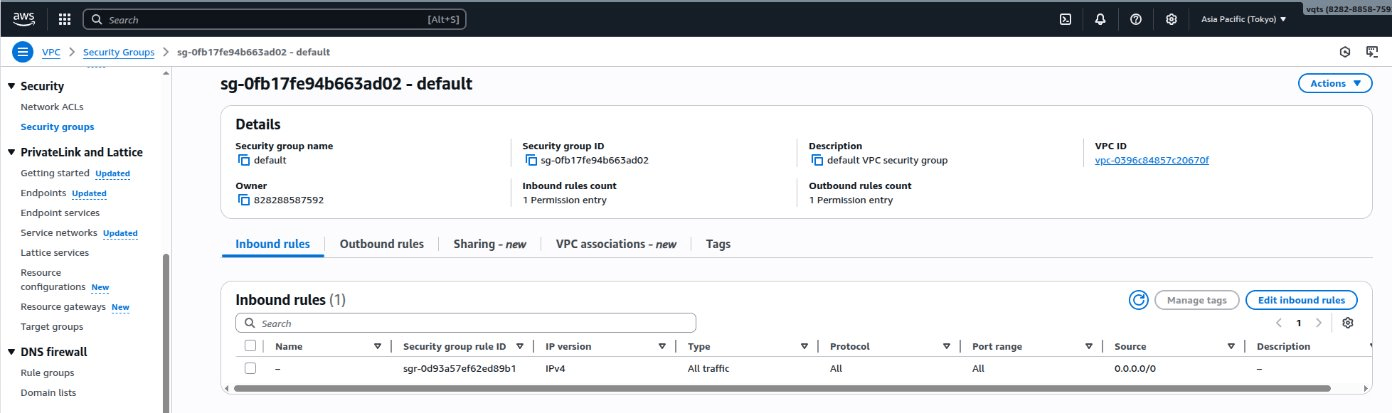 The Edit inbound rules page appears.
The Edit inbound rules page appears. - Click Add rule.
- Under Type, select All traffic.
- Under Source, select Anywhere-IPv4.
- Click Save rules.
AWS adds the security group to the QuWAN VPC.
F. Configure virtual private network (VPN) settings
- On the VPC dashboard side panel, go to Virtual private network (VPN) > Virtual private gateways.
- Click Create virtual private gateway.

- Specify a name tag for the VPN.
- Under Autonomous System Number (ASN), select Amazon default ASN.NoteThe ASN (Autonomous System Number) identifies AWS in the VPN connection. The default value is 64512, but it can be changed if it conflicts with your network.
- Optional: Define one or more tags to help identify the VPC subnet, and assign a value to each tag.
- Click Create virtual private gateway.
AWS creates the virtual private gateway. - On the Virtual private gateways page, select the virtual private gateway you configured.
- Click Actions, and then click Attach to VPC.
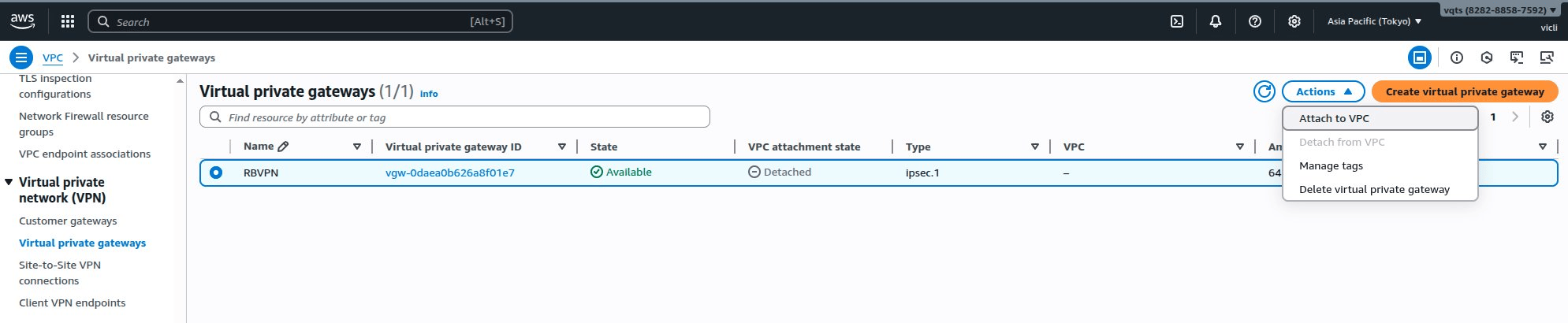 The Attach to VPC page appears.
The Attach to VPC page appears. - Click the search bar under Available VPCs, and then select the QuWAN VPC.
- Click Attach to VPC.
AWS attaches the configured virtual private gateway to the QuWAN VPC.
G. Identify the LAN and WAN IP address of your QNAP router
- Log in to QuRouter.
- Go to the WAN settings page:
- For QHora routers: Network > Physical Network Settings > WAN
- For QMiro routers: Network > WAN and LAN > WAN
- Identify the active WAN interface.
- Copy the IP address provided for the WAN interface.
- Go to the LAN settings page:
- For QHora routers: Network > Physical Network Settings > LAN
- For QMiro routers: Network > WAN and LAN > LAN
- Identify the active LAN interface.
- Copy the IP address provided for the LAN interface.
H. Add the virtual private gateway to the route table
- On the VPC dashboard side panel, go to Virtual private cloud > Route tables.
- Identify the route table associated with the QuWAN VPC.
- Click the route table ID.
The route table page appears. - Click Edit routes.
The Edit routes page appears.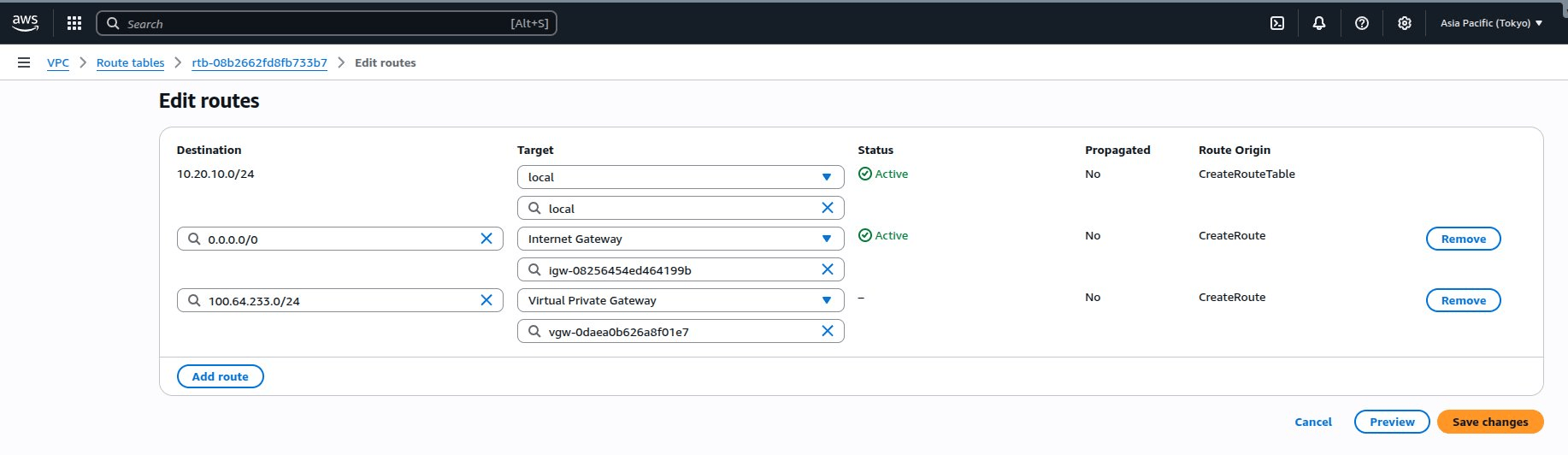
- Click Add route.
- Enter the copied QuRouter LAN interface IP address with its subnet in CIDR notation as the destination.
- Click the drop-down menu under Target, and select Virtual Private Gateway.
A secondary field appears appears under Internet Gateway. - Select the previously configured virtual private gateway from the drop-down menu.
- Click Save changes.
AWS updates the route table.
I. Create a customer gateway for the VPC
- On the VPC dashboard side panel, go to Virtual private network (VPN) > Customer gateways.
- Click Create customer gateway.
- Specify a name tag for the customer gateway.
- Enter the copied QuRouter WAN interface IP address in the IP address field.
- Optional: Click Add new tag to define one or more tags to help identify the customer gateway, and assign a value to each tag.
- Click Create customer gateway.
J. Create a site-to-site VPN connection
- On the VPC dashboard side panel, go to Virtual private network (VPN) > Site-to-site VPN connections.
- Click Create VPN connection.
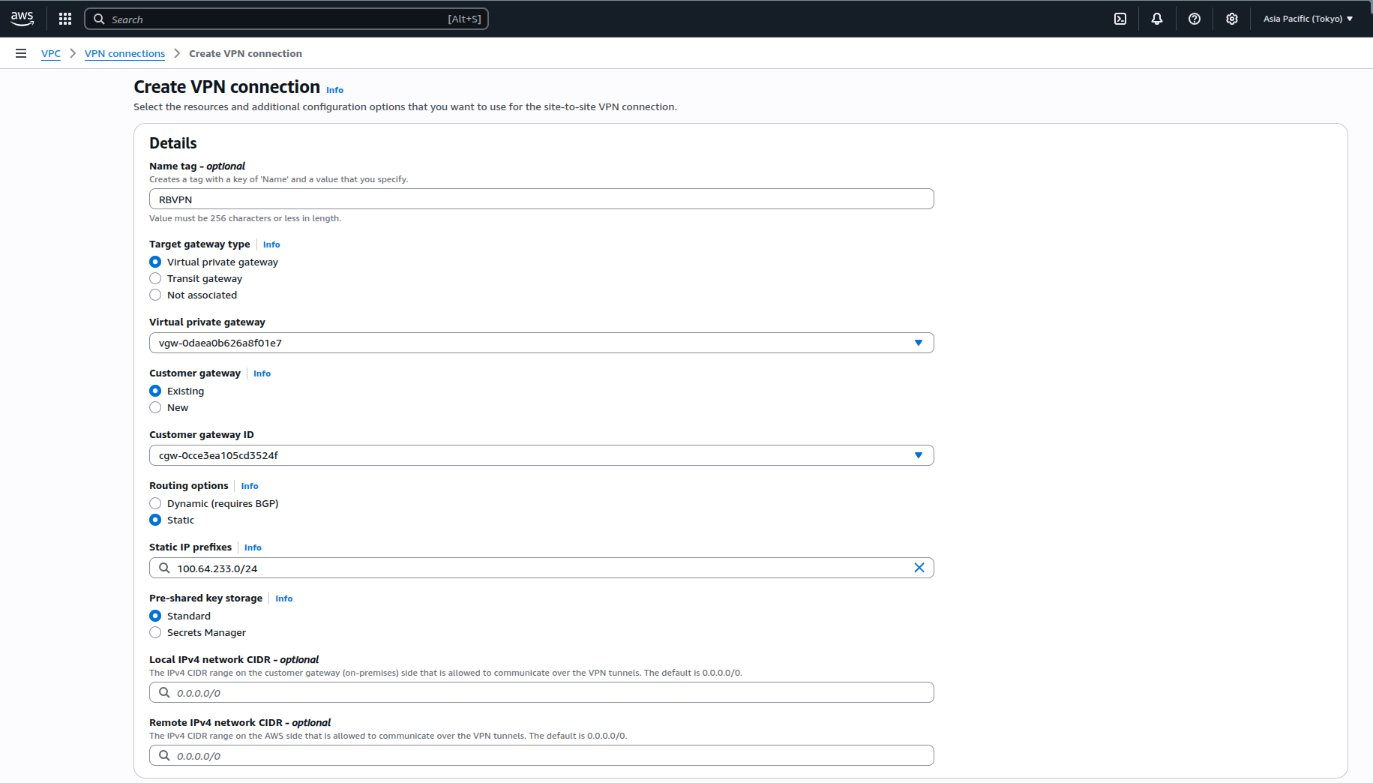
- Specify a name tag for the VPN connection.
- Under Target gateway type, select Virtual private gateway.
- Select the pre-configured virtual private gateway from the drop-down menu.
- Under Customer gateway, select Existing.
- Select the pre-configured customer gateway from the drop-down menu.
- Under Routing options, select Static.
- Enter the QuRouter LAN interface IP address with its subnet in CIDR notation in the
Add static IP prefixfield. - Optional: Configure the pre-shared key storage, local IPv4 network CIDR, remote IPv4 network CIDR fields.
- Optional: Configure the primary and secondary tunnel settings.
- Optional: Click Add new tag to define one or more tags to help identify the customer gateway, and assign a value to each tag.NoteAWS creates the Site-to-Site VPN connection with the QNAP router. On the VPN Connections page, verify that the connection status changes to
Available.
K. Download the site-to-site VPN configuration file
- On the VPC dashboard side panel, go to Virtual private network (VPN) > Site-to-site VPN connections.
- Identify the site-to-site VPN connection you created in the previous step.
- Select the VPN connection.
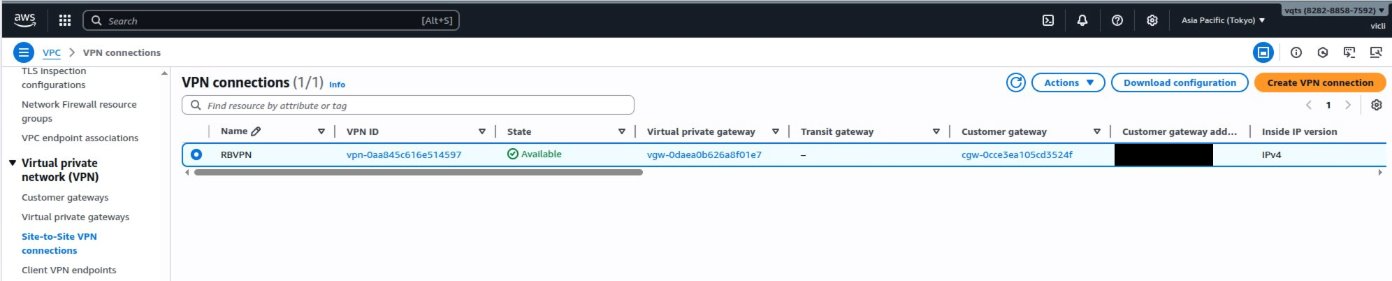
- Click Download configuration.
The Download configuration window appears. - Under Vendor, select Strongswan.
- Under IKE version, select ikev2.
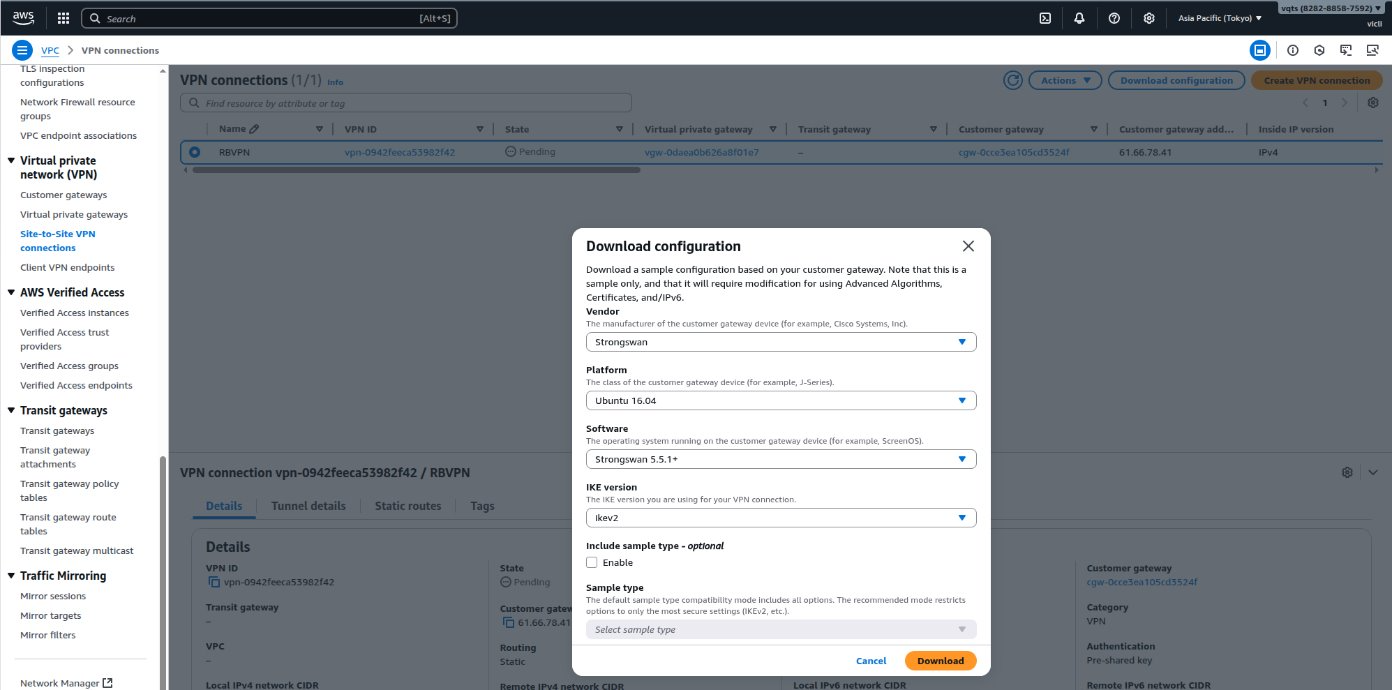
- Click Download.
The configuration file is downloaded in TXT format. - Click X on the Download configuration window.
Launch an EC2 (Elastic Cloud Compute) instance in AWS
- Go to https://console.aws.amazon.com/ec2/.
- On the side panel, go to Instances > Instances.
- Locate the Launch instances section.
- Click Launch instance.
The Launch an instance page appears. - Specify a name tag for the instance.
- Under Application and OS Images (Amazon Machine Image), click Ubuntu.
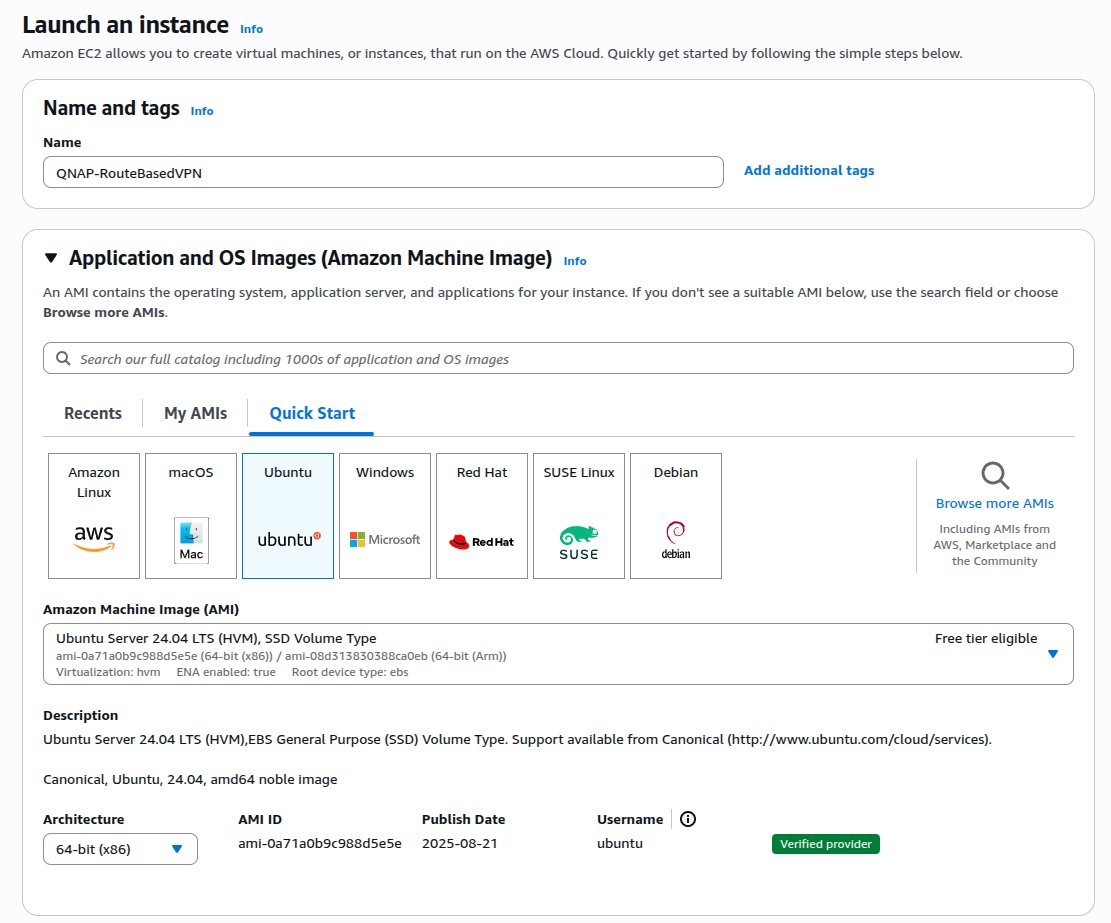
- Under Key pair (login), click Create new key pair.
The Create key pair window appears.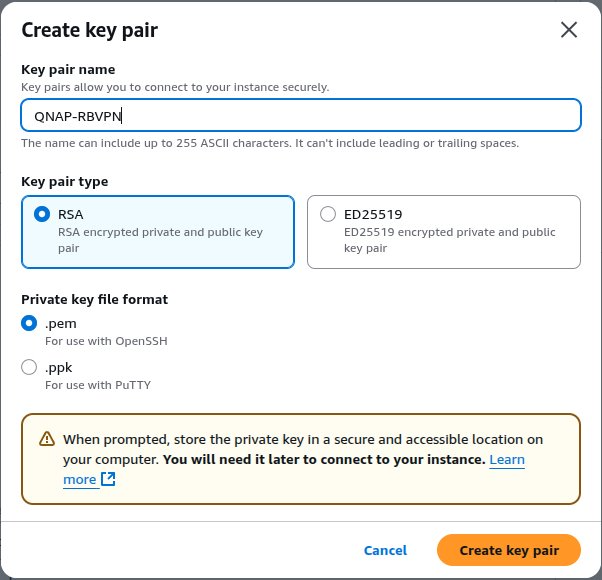
- Specify a name for the key pair.
- Under Key pair type, select RSA.
- Under Private key file format, select .pem.
- Click Create key pair.
AWS downloads the key pair configuration file in the selected format. - Select the previously configured key pair from the drop-down menu in the Key pair (login) section.
- Click Edit in the Network settings section.
- Under VPC - required, select the pre-configured VPC.
- Under Auto-assign public IP, select Enable.
- Under Firewall (security groups), select Select existing security group.

- Under Common security groups, select the previously configured security group.
- Optional: Configure the storage and advanced settings.
- Click Launch instance.
AWS launches the EC2 instance.
Configure site-to-site VPN settings in QuWAN Orchestrator
- Log in to QuWAN Orchestrator using your QNAP ID credentials.
- Select your organization.
- Go to QuWAN Topology > Route-Based VPN.
- Click Create New Connection.
The Create New Connection window appears. - Configure the route-based VPN connection settings.
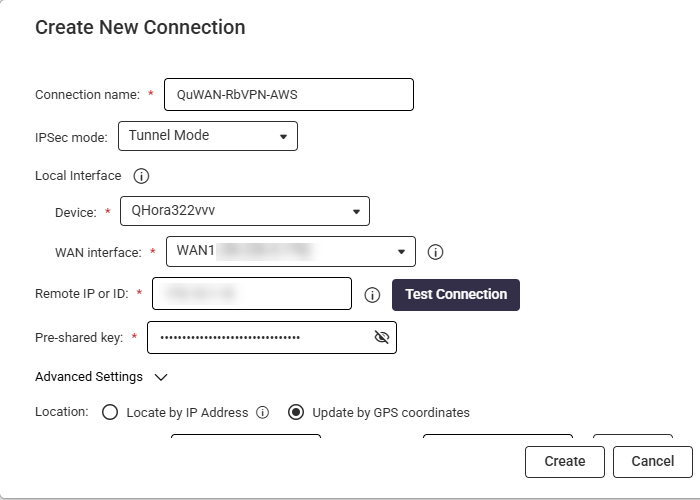
Setting Description Connection name Assign a descriptive name (e.g., AWS Site-to-Site VPN). IPsec mode Select Tunnel Mode. Device Designate the appropriate hub for the connection. WAN interface Enter the desired WAN interface. Remote IP or ID Specify the public IP address or hostname of the remote gateway device. Test Connection (Optional) Click to ping the device to confirm the connection. Pre-shared key Establish a strong pre-shared key, ensuring identical configuration on the remote gateway. - Click Advanced Settings to configure the advanced route-based VPN connection settings.
Setting User Action Example Value Internet Key Exchange (IKE) Version Select IKEv2. - Authentication algorithm Select a robust authentication algorithm. AES-128 Encryption Select a strong encryption method. AES-128 DH group Select the DH group size to determine the key strength used during the Diffie-Hellman exchange. 14 Security Association (SA) lifetime Define the IKE Security Association (SA) duration to reduce cryptographic risks associated with key exposure. 480 Local ID (Optional) Enter a local ID if you are using a Dynamic DNS (DDNS) service for the route-based VPN connection. - Encapsulating Security Payload (ESP) Authentication algorithm Select an authentication algorithm. SHA-256 Encryption Select an encryption method. AES-128 Enable Perfect Forward Secrecy (PFS) Enable to generate a new Diffie-Hellman (DH) key for each session, ensuring stronger security. - DH Group Select the DH group size to define the key strength for the VPN connection. 14 Security Association (SA) lifetime Define the SA lifetime duration to specify how long a security association remains valid before rekeying. 60 minutes Enable Dead Peer Detection (DPD) Enable to identity and respond to peer device outages. - DPD timeout Set the DPD timeout to define how long the device waits before considering the peer unresponsive. 10 seconds - Select a location setting to specify how the device’s position is determined:
- Locate by IP Address: Automatically detects the location based on the device’s IP address.
- Update by GPS coordinates: Requires users to manually provide the latitude and longitude values.
- Enable Enable NAT mode to ensure that the VPN connection functions properly even when NAT devices are present in the network.
- Specify the local tunnel IP address to facilitate NAT-traversal.
- Under Destination Configuration, click Add Subnet.
- Specify the internal subnet of the remote network you want to access.
- Click
 .
. - Click Create.NoteIf the route-based VPN connection is successful, the Status field displays the Connected status.



