How do I set up site-to-site VPN between a QuWAN and Fortinet® device?
Applicable Products
- QuWAN Orchestrator
- QuRouter 2.4.0 or later versions
- Fortinet ® FortiGate® device
Details
This tutorial guides you through establishing a site-to-site VPN connection between a QNAP router that has been added to a QuWAN network and a Fortinet ® FortiGate® device. By configuring VPN settings on both devices, you can create a secure and reliable connection between two networks, enabling data transfer and remote access. This guide provides step-by-step instructions for configuring, verifying, and managing the VPN connection to ensure proper network integration and security.
- QuWAN site-to-site VPN only supports IKEv2.
- The QuWAN-connected router and Fortinet ® FortiGate® device must be configured with identical settings to ensure proper VPN operation.
- Your QNAP device must be added to QuWAN Orchestrator before configuring the site-to-site VPN. Refer to the QuWAN and QuWAN Orchestrator Help for adding your device: Configuration | QuWAN and QuWAN Orchestrator Help (qnap.com)
Implementing a site-to-site VPN introduces additional complexity to your network. Ensure you understand the security implications before enabling it.
Procedure
Configure the FortiGate® IPSec VPN settings
Configure the following settings on your FortiGate® device to establish an IPsec site-to-site VPN tunnel with your QuWAN-connected router. Define the authentication method, encryption algorithms, and key exchange settings to ensure a secure connection. Enable options like NAT traversal and dead peer detection to maintain tunnel stability and compatibility with QuWAN’s VPN framework. The following settings below are based on the FortiProxy 1.1.0 Online Help for a FortiGate® 300C device.
- Log in to the FortiGate® user interface.
- Go to VPN > IPSec > Tunnels.
- Click Create New.
- Configure the IPSec VPN settings.
General Settings
Setting User Action Name Enter a unique name for the VPN tunnel. Comments (Optional) Add a description for the tunnel. Enable IPsec Interface Mode Select to enable IPsec for the VPN tunnel. Network Settings
Setting User Action IP Version Select IPv4 as the protocol version. Remote Gateway Choose Static IP Address if the remote peer has a fixed IP. IP Address Enter the remote peer's IP address. Interface Select the network interface for the VPN tunnel. Mode Config (Optional) Enable to assign IP addresses to VPN clients. NAT Traversal Enable NAT Traversal if a NAT device is between the peers. Keepalive Frequency Set how often keepalive packets are sent. Dead Peer Detection Enable dead peer detection to detect and remove unresponsive VPN peers. 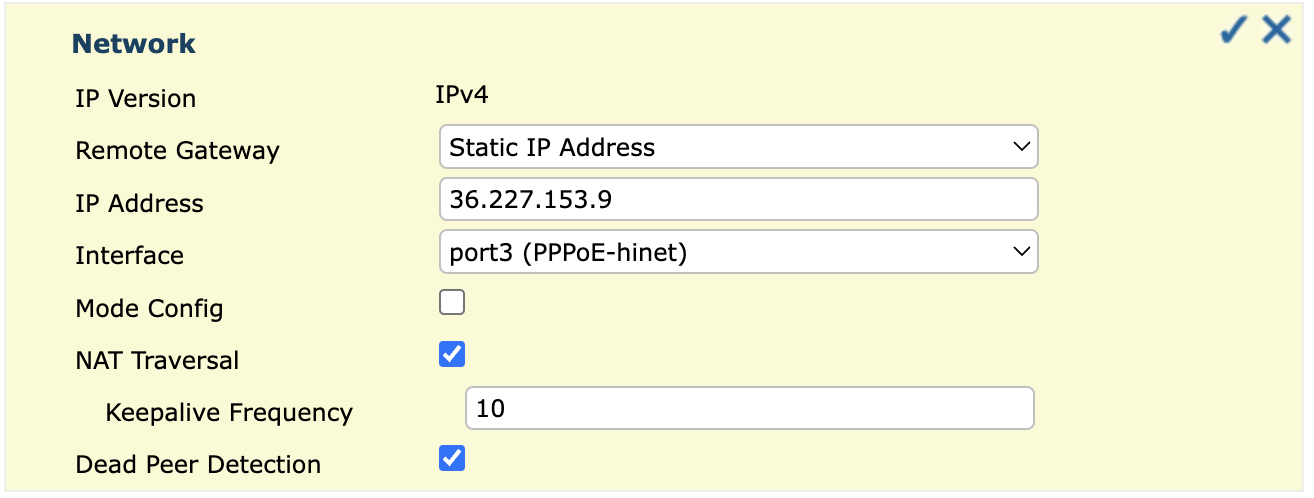
Authentication Settings
Setting User Action Method Select Pre-shared Key for authentication. Pre-shared Key Copy the pre-shared key from the route-based VPN connection configuration window in QuWAN Orchestrator and paste it in the pre-shared key field. IKE Version Select 2 for the IKE version. Mode Select Main (ID Protection) for secure identity handling. 
Phase 1 Proposal Settings
NoteEnsure that both devices have matching encryption and authentication settings.Setting User Action Encryption Select encryption algorithm AES256. Authentication Select SHA256 for authentication. Diffie-Hellman Groups Select key exchange groups such as 2, 5, 14, 15, 16, 19, 20, or 21. Key Lifetime (seconds) Set how long the encryption key remains valid (default: 86400 seconds). Local ID Enter a local ID if required.
If you are using a Dynamic DNS (DDNS) service for a route-based IPsec VPN connection, you must set the local ID in FQDN format.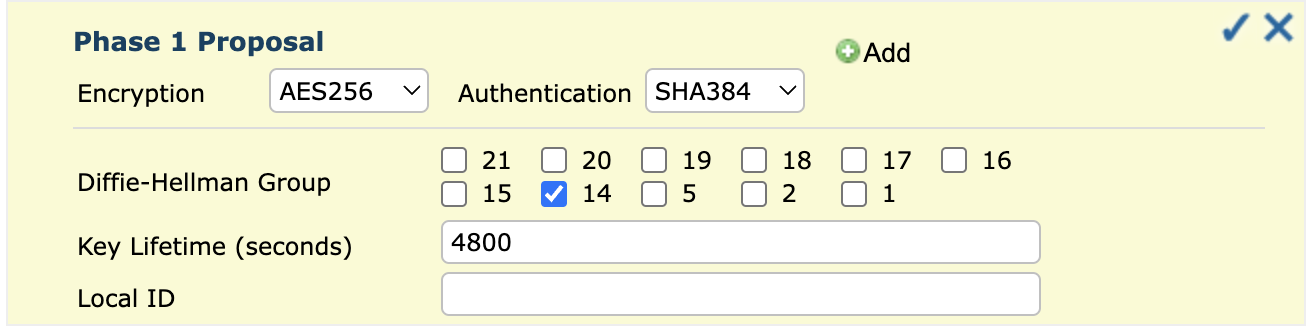
XAUTH Settings
Setting User Action Type Select Disabled unless extended authentication is needed. Phase 2 Selectors
Setting User Action Local Address Define the local network (default: 0.0.0.0/0). Remote Address Define the remote network (default: 0.0.0.0/0). 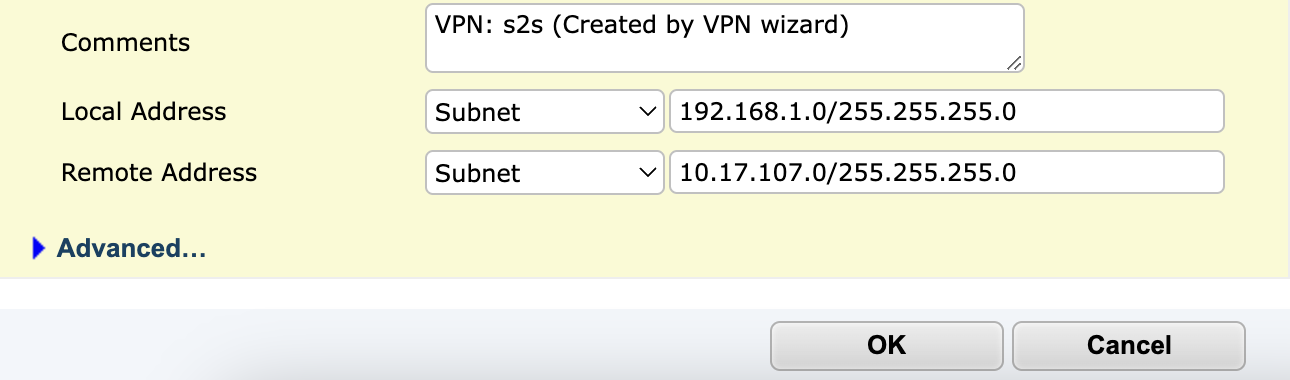
Phase 2 Settings
Setting User Action Name Keep the same name as Phase 1 or modify it if needed. Comments (Optional) Add a description. Local Address Select Subnet and configure the local network range. Remote Address Select Subnet and configure the remote network range. - Click OK.
The FortiGate® device creates the IPSec VPN tunnel.
Create a route-based VPN connection in QuWAN Orchestrator
To connect a QuWAN-connected router to a FortiGate® device, you must configure a route-based VPN. This method establishes an encrypted tunnel that directs traffic between the two networks based on routing policies. Unlike policy-based VPNs, route-based VPNs support dynamic routing and multiple subnets, ensuring precise traffic control and efficient data exchange between the connected sites.
Before configuring a route-based VPN connection in QuWAN Orchestrator, ensure proper configuration on the peer device. This refers to the device at the other end of the VPN tunnel, such as another router or firewall.
- Log in to QuWAN Orchestrator.
- Go to QuWAN Topology > Route-Based VPN.
- Click Create New Connection.
The Create New Connection window appears.
- Specify a connection name between 1 and 64 characters.
- Select Tunnel Mode as the IPSec mode.
- Select a hub to route traffic and central management.
- Select the WAN interface port.
- Specify the public IP address or hostname of the remote gateway device.
- Click Test Connection to test the remote gateway connection.
- Specify a pre-shared key.NoteEnsure the pre-shared key on the remote device is identical to the one configured in QuWAN Orchestrator.
- Optional: Click Advanced Settings to reveal additional configuration options for route-based VPN connections.
- Configure the Internet Key Exchange (IKE) settings:
- Select the IKE version.
- Select the authentication algorithm.
- Select a suitable encryption method.
- Select a Diffie-Hellman (DH) group.NoteDH groups define the cryptographic strength to securely establish a private key during initial communication.
- Define the IKE Security Association (SA) duration to reduce cryptographic risks associated with key exposure.
- Optional: Specify the local ID (domain name) for remote site authentication.
- Provide the local ID only if DDNS is configured for the route-based VPN connection.
- Configure the Encapsulating Security Payload (ESP) settings:
- Select the authentication algorithm.
- Select a suitable encryption method.
- Select Enable Perfect Forward Secrecy (PFS) to generate a new DH key.
- Select a DH group.
- Define the ESP SA duration.
- Optional: Select Enable Dead Peer Detection (DPD) to identify and respond to peer device outages.
- Specify the DPD timeout value in seconds.
- Optional: Select Enable NAT mode to ensure that the VPN connection functions properly even when NAT devices are present in the network.
- Specify the local tunnel IP address to facilitate NAT traversal.
- Optional: Configure the site subnet settings:
- Under Site Subnets, click Add Subnet.
- Specify a site subnet.
- Specify a description.
- Click
 .
.
- Click Create.
QuWAN Orchestrator creates the route-based VPN connection. - Identify the FortiGate® route-based VPN connection in the QuWAN Topology/Route-based VPN page.
- Click
 to enable the route-based VPN connection.
to enable the route-based VPN connection.
QuWAN Orchestrator establishes the site-to-site VPN connection between the QNAP router and the Fortinet® FortiGate® device.
Further Reading
- QuWAN and QuWAN Orchestrator Web Help
- QuRouter Web Help for QHora routers
- Fortinet® Documentation
- How do I set up site-to-site VPN between a QuWAN and Cisco® Meraki® device?
- How do I set up site-to-site VPN between a QuWAN and UniFi® device?
- How do I securely transmit data between a site-to-site IPSec VPN and a third-party network using a route-based VPN in QuWAN Orchestrator?





