How to Configure WireGuard VPN Server and Client Settings in QuRouter
- How to Configure WireGuard VPN Server and Client Settings in QuRouter
- WireGuard
- Enabling a WireGuard VPN Server
- Adding a WireGuard VPN User
- Connecting to WireGuard on Windows 10
- Connecting to WireGuard on macOS 10.13
- Connecting to WireGuard on iOS
- Connecting to WireGuard on Android 7.0
How to Configure WireGuard VPN Server and Client Settings in QuRouter
This tutorial explains how to configure WireGuard on your QNAP router using QuRouter.
WireGuard
WireGuard is an open-source VPN protocol that uses User Datagram Protocol (UDP) for network communication. The protocol uses several cryptography tools to implement secure VPN tunneling.
Enabling a WireGuard VPN Server
QuRouter enables the WireGuard server.
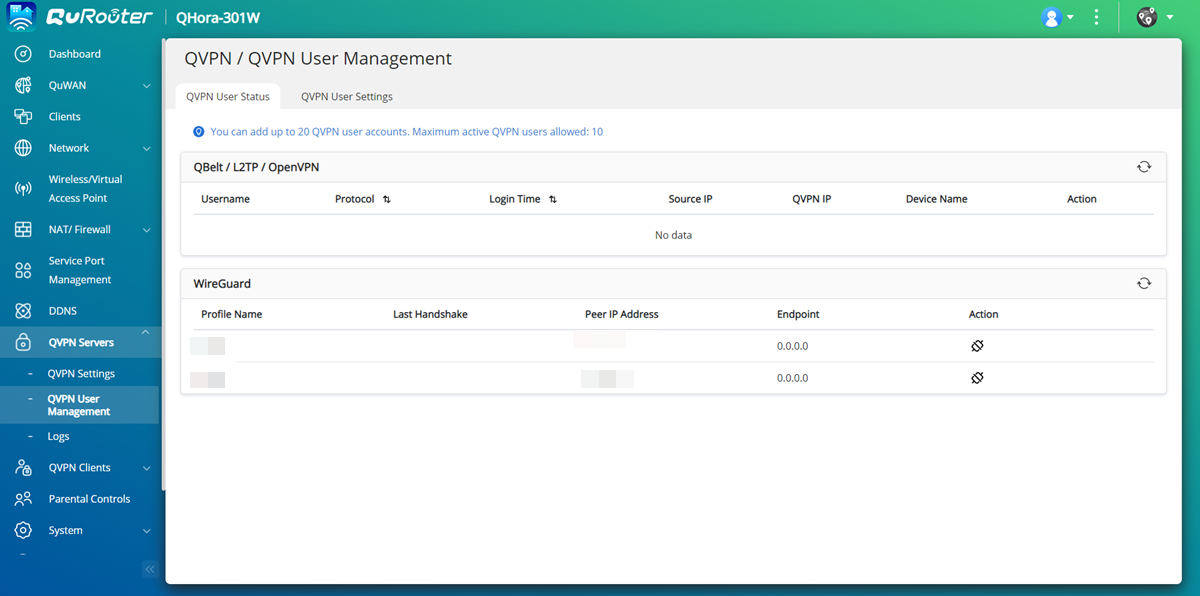
Adding a WireGuard VPN User
Connecting to WireGuard on Windows 10
Download and install WireGuard from the WireGuard website.
The WireGuard application establishes a VPN tunnel with the VPN server.

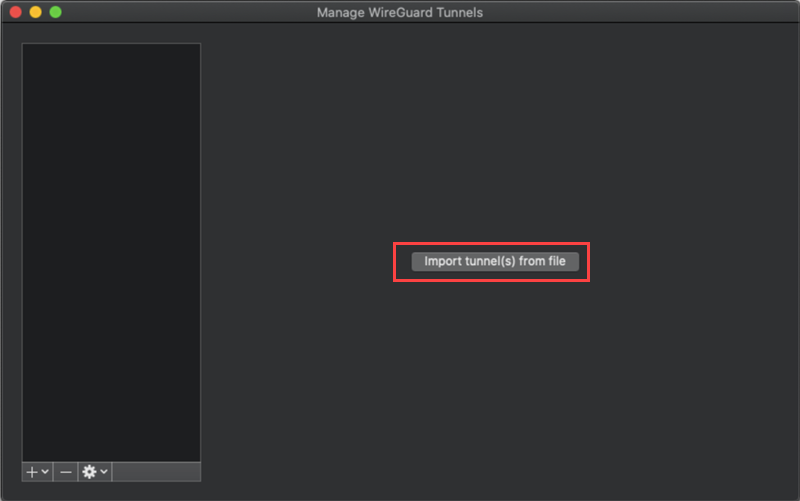
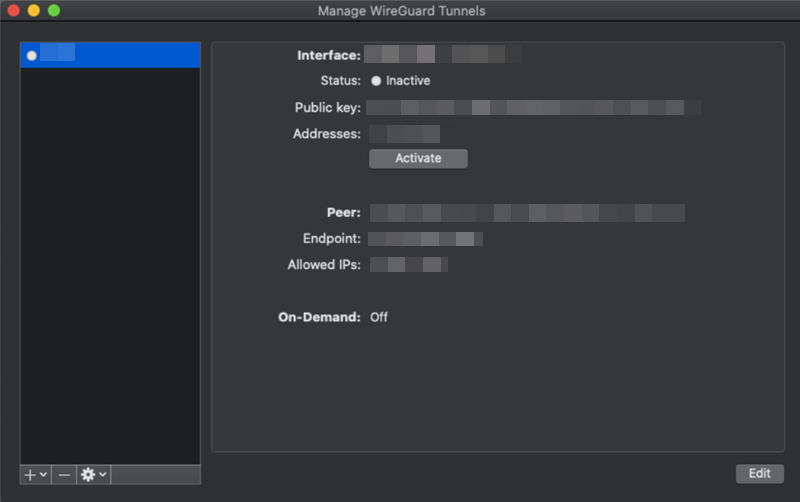
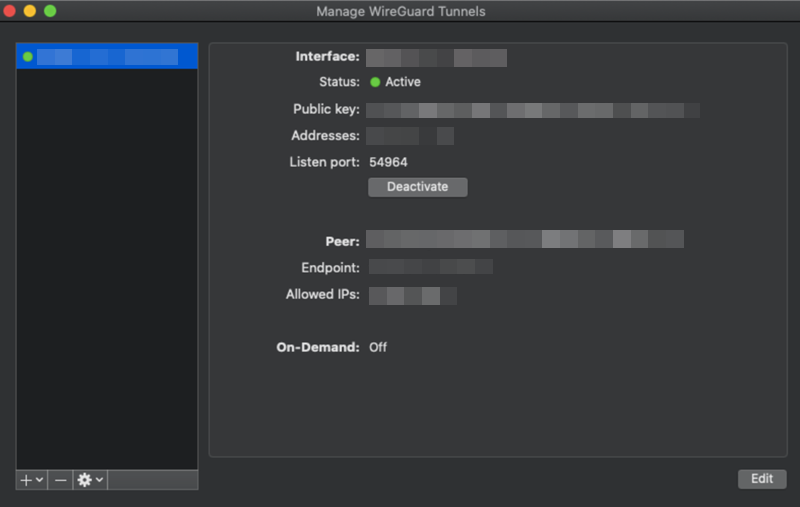
Connecting to WireGuard on macOS 10.13
Download and install WireGuard from the WireGuard website.
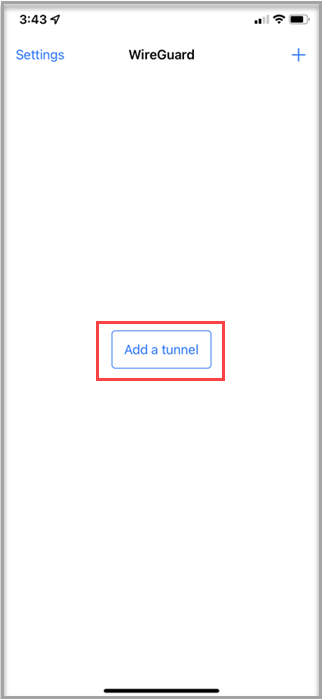
Connecting to WireGuard on iOS
Download and install WireGuard from the WireGuard website.
The WireGuard app establishes a VPN tunnel with the VPN server.

Connecting to WireGuard on Android 7.0
Download and install WireGuard from the WireGuard website.
WireGuard establishes a VPN tunnel with the VPN server.

 .
.
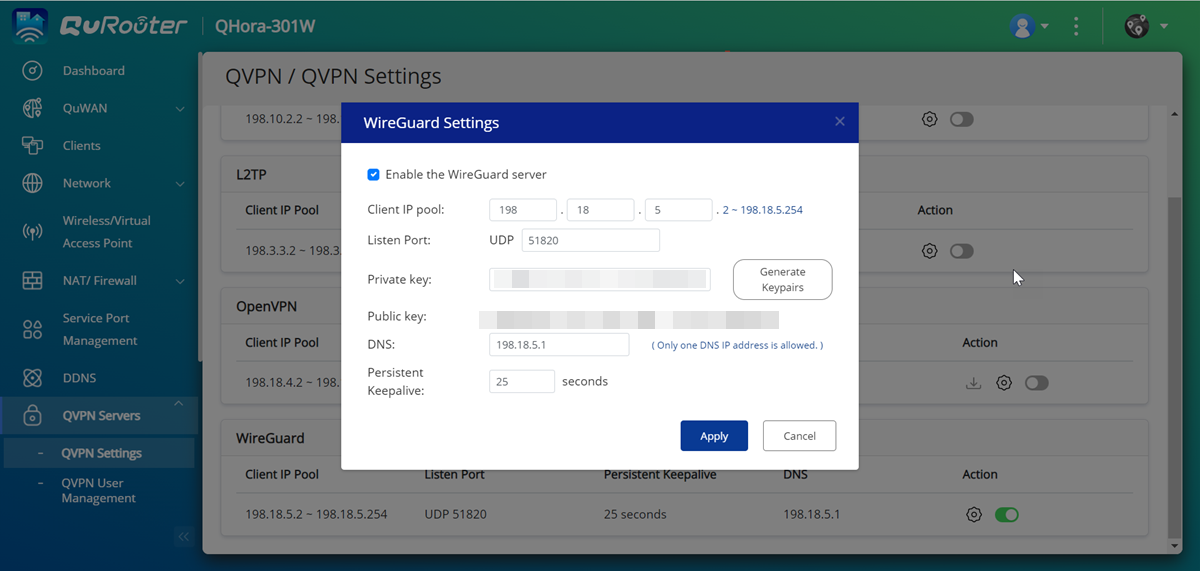
 .
.

 .
.
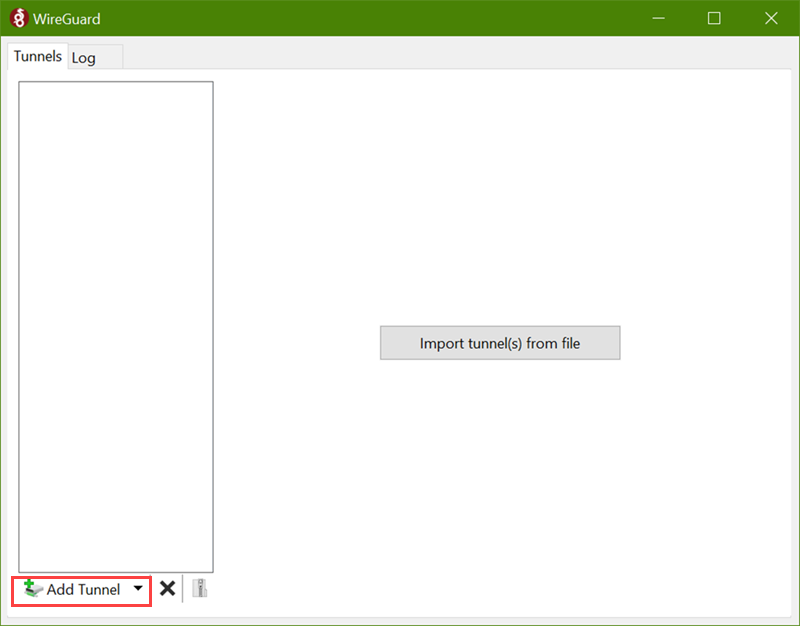


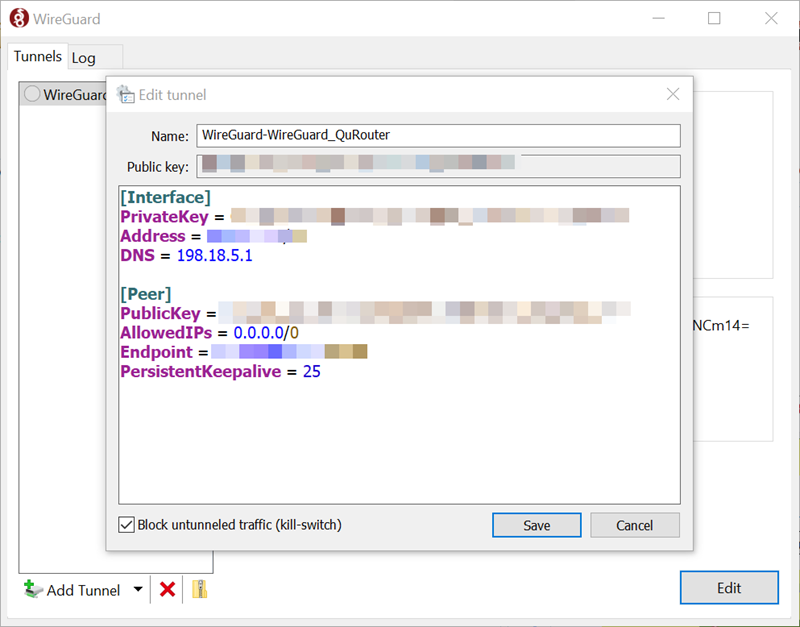








 .
.
 .
.
 to generate the private key for the VPN connection.
to generate the private key for the VPN connection.
 .
. .
.




