Applicable Products
Hardware
Software
- QuRouter 2.4.2 and later versions
Overview
This tutorial explains how QuRouter utilizes mutual TLS (mTLS) and its certificates to facilitate secure communication between multiple QNAP products and services. By implementing mTLS, QuRouter enhances data protection and provides strong security for corporate networks.
What is mTLS?
Mutual TLS (mTLS) is an enhanced version of Transport Layer Security (TLS), a cryptographic protocol designed to authenticate both parties in a network connection. In contrast to standard TLS, which verifies only the server's identity, mTLS ensures that both the client and server authenticate each other. This two-way authentication is achieved by confirming that both sides hold valid private keys corresponding to their certificates. As a result, mTLS strengthens the trust between devices and services.
What certificate authorities (CAs) are used by mTLS?
A root TLS certificate is essential in mTLS for establishing a trusted connection. This certificate enables an organization to operate as its own certificate authority. Every certificate used by authorized clients and servers must be linked to this root certificate. As a self-signed certificate, the root certificate is created and managed by the organization itself, forming the basis for authenticating devices and services within the network.
Why does QuRouter use mTLS?
QuRouter adopts mTLS to provide secure communication between services, incorporating both encryption and mutual authentication. This approach utilizes certificates to bolster security within corporate networks and facilitate integration with QNAP products, such as the Airgap+ backup solution paired with Hybrid Backup Sync.
In the case of QuRouter, mTLS is vital for establishing a trusted communication pathway. For example, during the setup of Airgap+, the Hybrid Backup Center relies on mTLS to interact with QuRouter, enabling it to securely manage the port link status while ensuring authenticated communication.
How to configure mTLS in QuRouter?
- Log in to QuRouter.
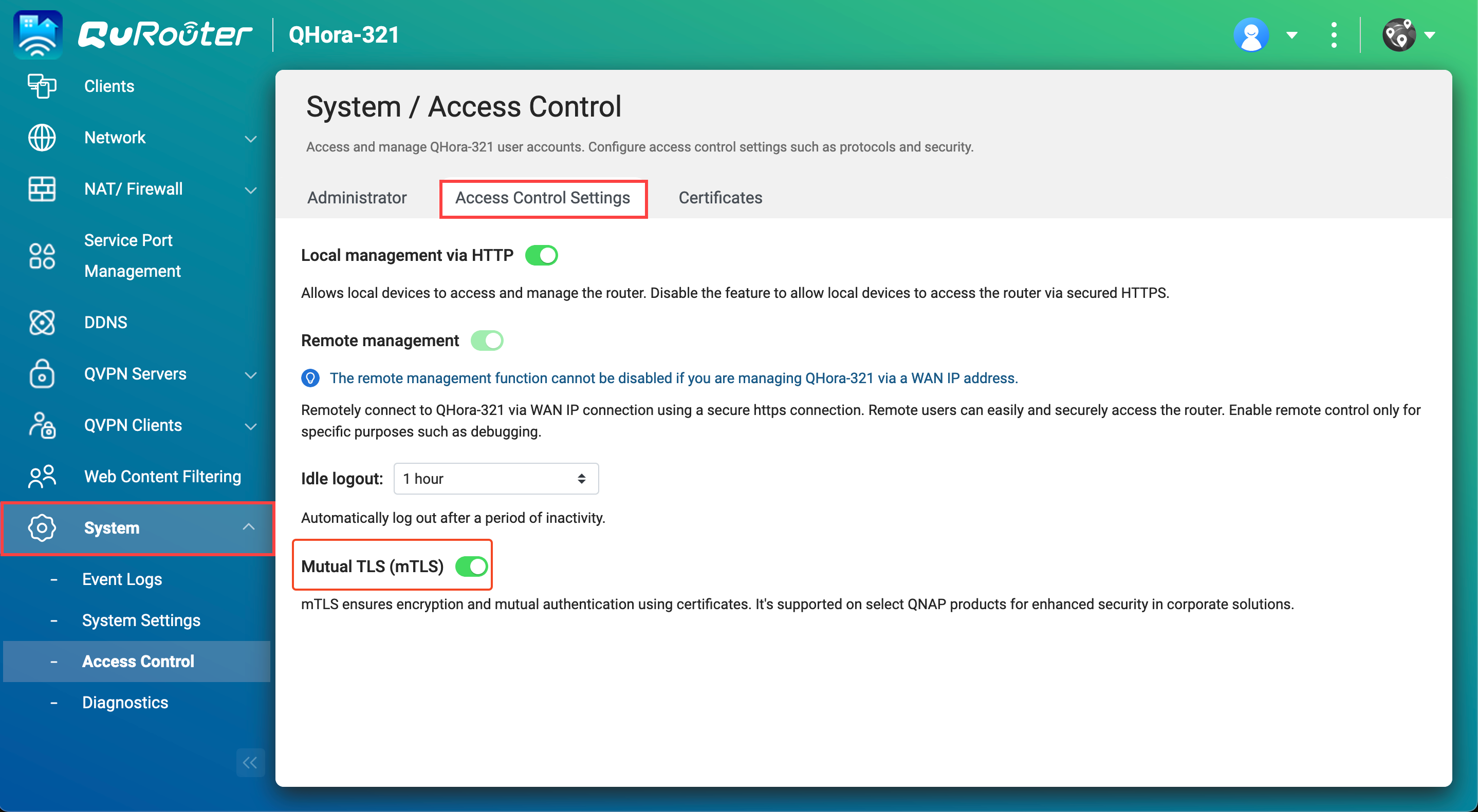
- Go to System > Access Control > Access Control Settings.
- Next to Mutual TLS (mTLS), click
 .
.
Note
When you enable mTLS, QuRouter requires certificates to access its web interface, as part of the mTLS mechanism. To keep logging in with just your account and password, simply cancel any certificate prompts that appear in your browser. Typically, the certificate prompt appears only once and does not return after being canceled, but it may reappear after you restart your PC.
 An example of a certificate selection prompt displayed in QuRouter.
An example of a certificate selection prompt displayed in QuRouter. How to manage signed certificates in QuRouter?
You can view signed certificates in QuRouter or revoke a certificate to prevent the service from communicating with QuRouter and managing the router.
- Log in to QuRouter.
- Navigate to System > Access Control > Certificates.
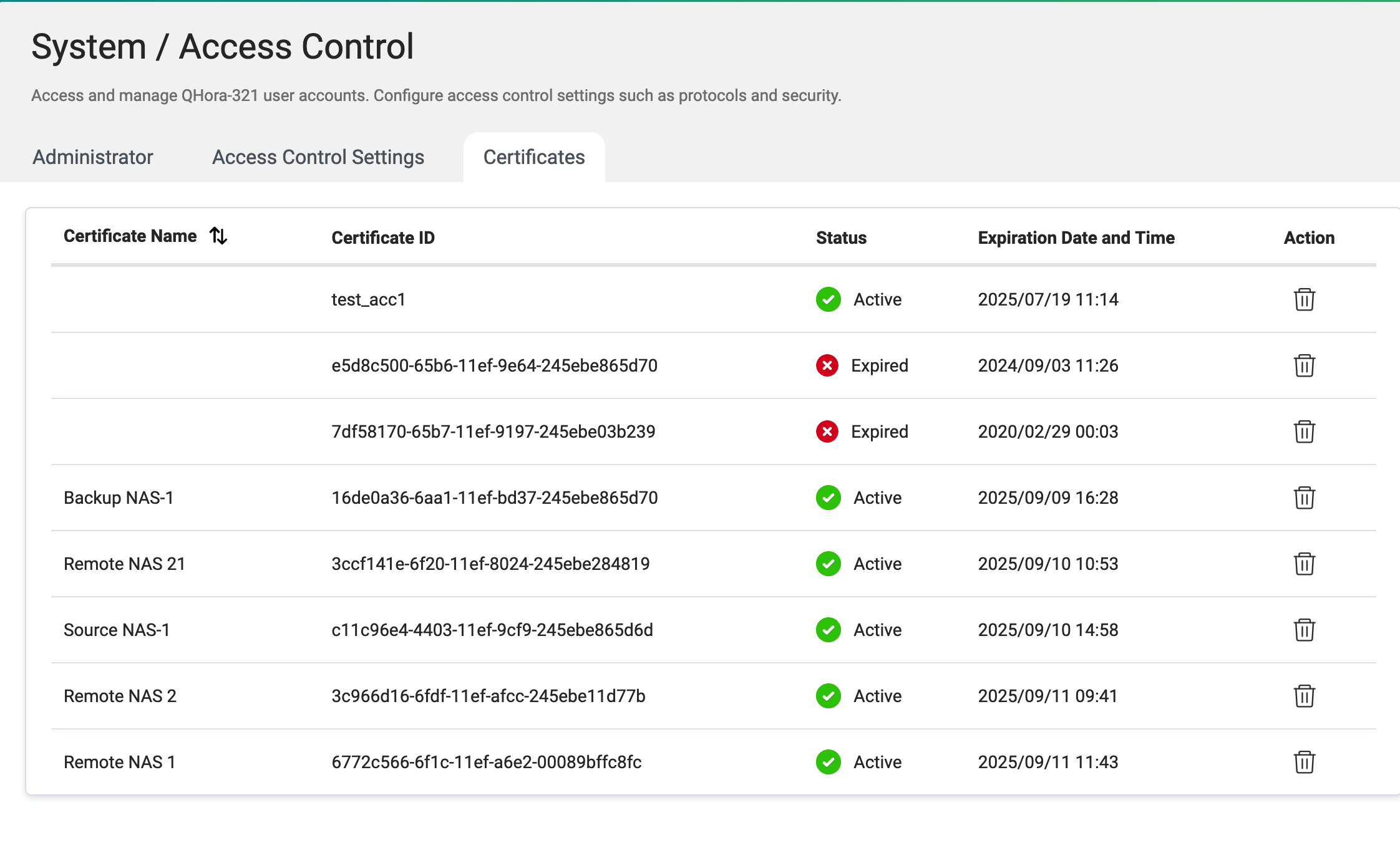
Note
To revoke a certificate, click

.
Further Reading
How to Set Up Airgap+ to Protect Your HBS Backups
Gældende produkter
Hardware
Software
- QuRouter 2.4.2 og senere versioner
Oversigt
Denne vejledning forklarer, hvordan QuRouter anvender mutual TLS (mTLS) og dets certifikater til at lette sikker kommunikation mellem flere QNAP-produkter og -tjenester. Ved at implementere mTLS forbedrer QuRouter databeskyttelsen og giver stærk sikkerhed for virksomhedsnetværk.
Hvad er mTLS?
Mutual TLS (mTLS) er en forbedret version af Transport Layer Security (TLS), en kryptografisk protokol designet til at autentificere begge parter i en netværksforbindelse. I modsætning til standard TLS, som kun verificerer serverens identitet, sikrer mTLS, at både klienten og serveren autentificerer hinanden. Denne tovejsautentificering opnås ved at bekræfte, at begge parter har gyldige private nøgler, der svarer til deres certifikater. Som et resultat styrker mTLS tilliden mellem enheder og tjenester.
Hvilke certifikatudstedere (CAs) anvendes af mTLS?
Et root TLS-certifikat er essentielt i mTLS for at etablere en betroet forbindelse. Dette certifikat gør det muligt for en organisation at fungere som sin egen certifikatudsteder. Hvert certifikat, der bruges af autoriserede klienter og servere, skal være knyttet til dette root-certifikat. Som et selvsigneret certifikat oprettes og administreres root-certifikatet af organisationen selv og danner grundlaget for autentificering af enheder og tjenester inden for netværket.
Hvorfor bruger QuRouter mTLS?
QuRouter anvender mTLS for at sikre kommunikation mellem tjenester, der inkorporerer både kryptering og mutual autentificering. Denne tilgang anvender certifikater til at styrke sikkerheden inden for virksomhedsnetværk og lette integrationen med QNAP-produkter, såsom Airgap+ backup-løsningen parret med Hybrid Backup Sync.
I tilfælde af QuRouter er mTLS afgørende for at etablere en betroet kommunikationsvej. For eksempel, under opsætningen af Airgap+, er Hybrid Backup Center afhængig af mTLS for at interagere med QuRouter, hvilket gør det muligt at administrere portforbindelsesstatus sikkert, samtidig med at det sikrer autentificeret kommunikation.
Hvordan konfigureres mTLS i QuRouter?
- Log ind på QuRouter.
- Gå til System >Adgangskontrol > Adgangskontrol Indstillinger.
- Ved siden af Mutual TLS (mTLS), klik.


Bemærk
Når du aktiverer mTLS, kræver QuRouter certifikater for at få adgang til dets webinterface som en del af mTLS-mekanismen. For at fortsætte med at logge ind med blot din konto og adgangskode, skal du blot annullere eventuelle certifikatprompter, der vises i din browser. Typisk vises certifikatprompten kun én gang og vender ikke tilbage efter at være blevet annulleret, men den kan dukke op igen efter du genstarter din PC.
 Et eksempel på en certifikatvalgsprompt vist i QuRouter.
Et eksempel på en certifikatvalgsprompt vist i QuRouter. Hvordan administreres signerede certifikater i QuRouter?
Du kan se signerede certifikater i QuRouter eller tilbagekalde et certifikat for at forhindre tjenesten i at kommunikere med QuRouter og administrere routeren.
- Log ind på QuRouter.
- Gå til System >Adgangskontrol >Certifikater.

Bemærk
For at tilbagekalde et certifikat, klik.

Yderligere læsning
Sådan opsættes Airgap+ for at beskytte dine HBS-backups


 Et eksempel på en certifikatvalgsprompt vist i QuRouter.
Et eksempel på en certifikatvalgsprompt vist i QuRouter. 






