Why do some NAS applications malfunction after I allow connections only from a specific list?
Applicable Products
Container Station
Scenario
When the Allow connections from the list only option is enabled, the device restricts network access to a predefined set of IP addresses or subnets. This security measure operates at the IP layer (Layer 3) and is designed to reduce vulnerabilities by permitting only trusted connections. However, some NAS applications may malfunction under this setting because they often rely on inter-network communication between different segments within the device.
For instance, applications running in containers or deployed through Container Station might need to communicate with external services or other internal modules that are not included in your approved list. If these necessary connections are inadvertently blocked, the application can experience disruptions or fail to operate correctly. To prevent these issues, it is important to carefully review and update your allowed list to include all IP addresses or subnets required by your applications.
Procedure
Follow these steps to configure network connectivity:
- Log in to your QNAP device and open Network & Virtual Switch.
- Select Advanced mode.
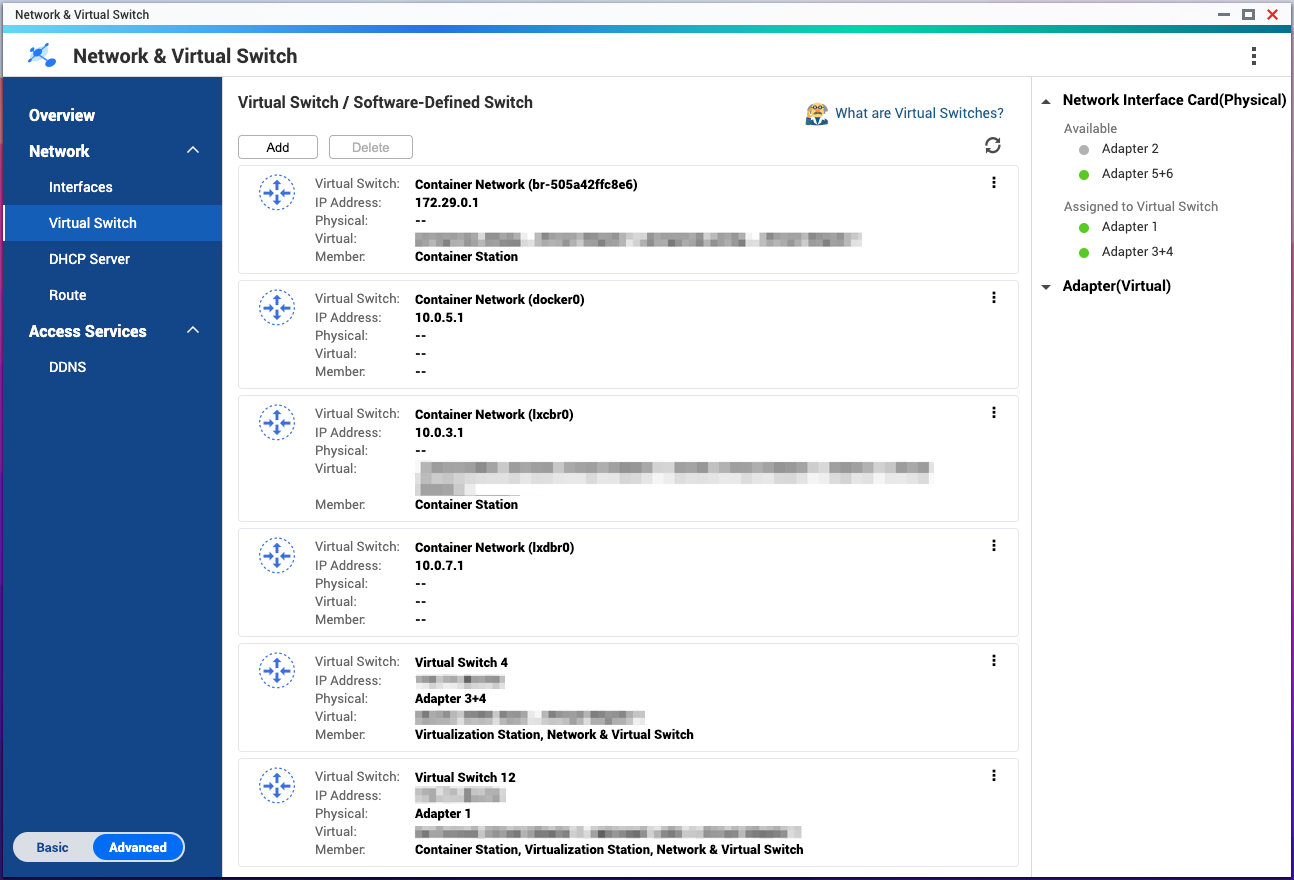
- Go to Network > Virtual Switch.
- Identify the network segments used by the container network.
- Go to Control Panel > System > Security > Allow/Deny List.NoteIf QuFirewall is installed on your device, ensure it is enabled, then open QuFirewall and add the required network segments to the allow list.
- Ensure that the container network segments are added to the allow list.
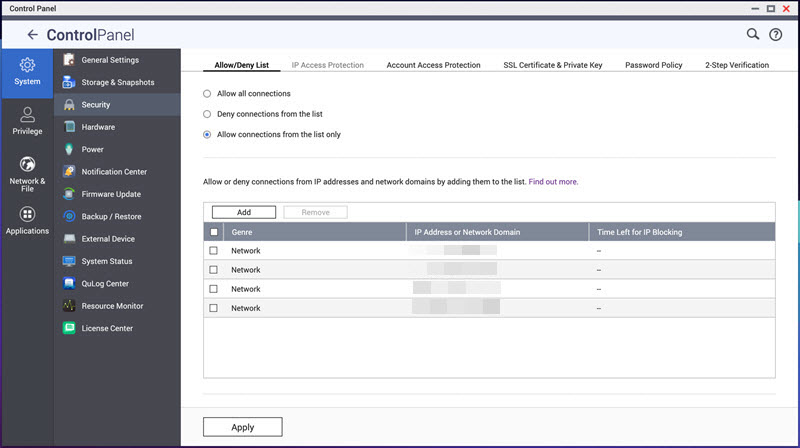 ImportantQNAP strongly recommends adding the following IP ranges to the allow list:
ImportantQNAP strongly recommends adding the following IP ranges to the allow list:10.0.3.0/24,10.0.5.0/24,10.0.7.0/24,172.29.0.0/22,172.30.0.0/22. If Kubernetes services are enabled, also add10.42.0.0/24(Kubernetes Pod Network CIDR).


